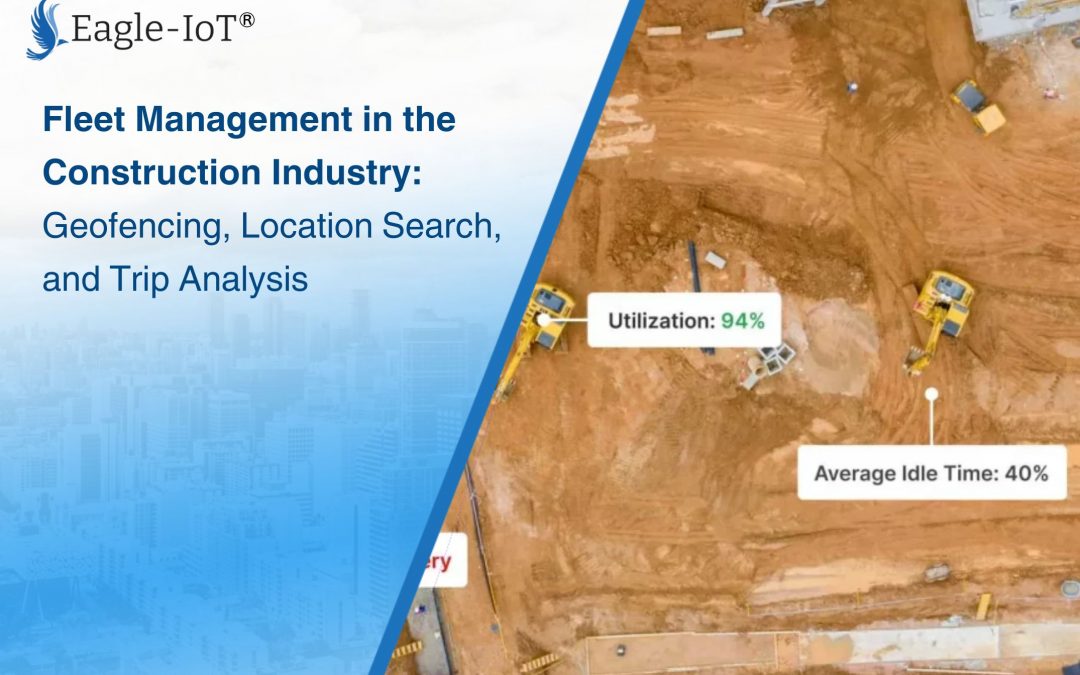
Fleet Management in the Construction Industry: Geofencing, Location Search, and Trip Analysis
In the dynamic world of construction, efficiency and precision are key to managing multiple projects, assets, and workforces spread across various locations. The need for real-time monitoring, quick decision-making, and asset optimization has led to a significant reliance on telematics and fleet management technologies. Among these, features such as geofencing, location search, route planning, and trip analysis have emerged as essential tools for fleet managers in the construction industry.
This article will dive into how construction companies can leverage advanced features like geofencing, location search, route planning, and multi-vehicle tracking to boost operational efficiency, minimize risks, and enhance asset utilization.
Geofencing and Location Search: Defining Boundaries and Optimizing Fleet Management
Visualizing and Managing Geofences
Geofencing is a powerful feature that allows construction companies to define geographic boundaries, which can be used for a variety of purposes, from monitoring assets to improving security and enforcing operational protocols. With the ability to view, create, and hide geofences, fleet managers can define boundaries around key areas, such as construction sites, warehouses, or restricted zones, and receive alerts when vehicles or assets enter or exit these predefined zones.

For instance, you can create a geofence around your primary construction site to monitor which vehicles are arriving and leaving, ensuring that only authorized vehicles enter the site. Similarly, you can designate a geofence around restricted areas, where unauthorized access could lead to accidents or violations of safety protocols.
Each geofence can be configured with specific settings, such as speed restrictions, entry/exit alerts, and operational rules. This flexibility allows construction companies to tailor geofencing to meet their unique operational requirements, making it an indispensable tool for project and site management.
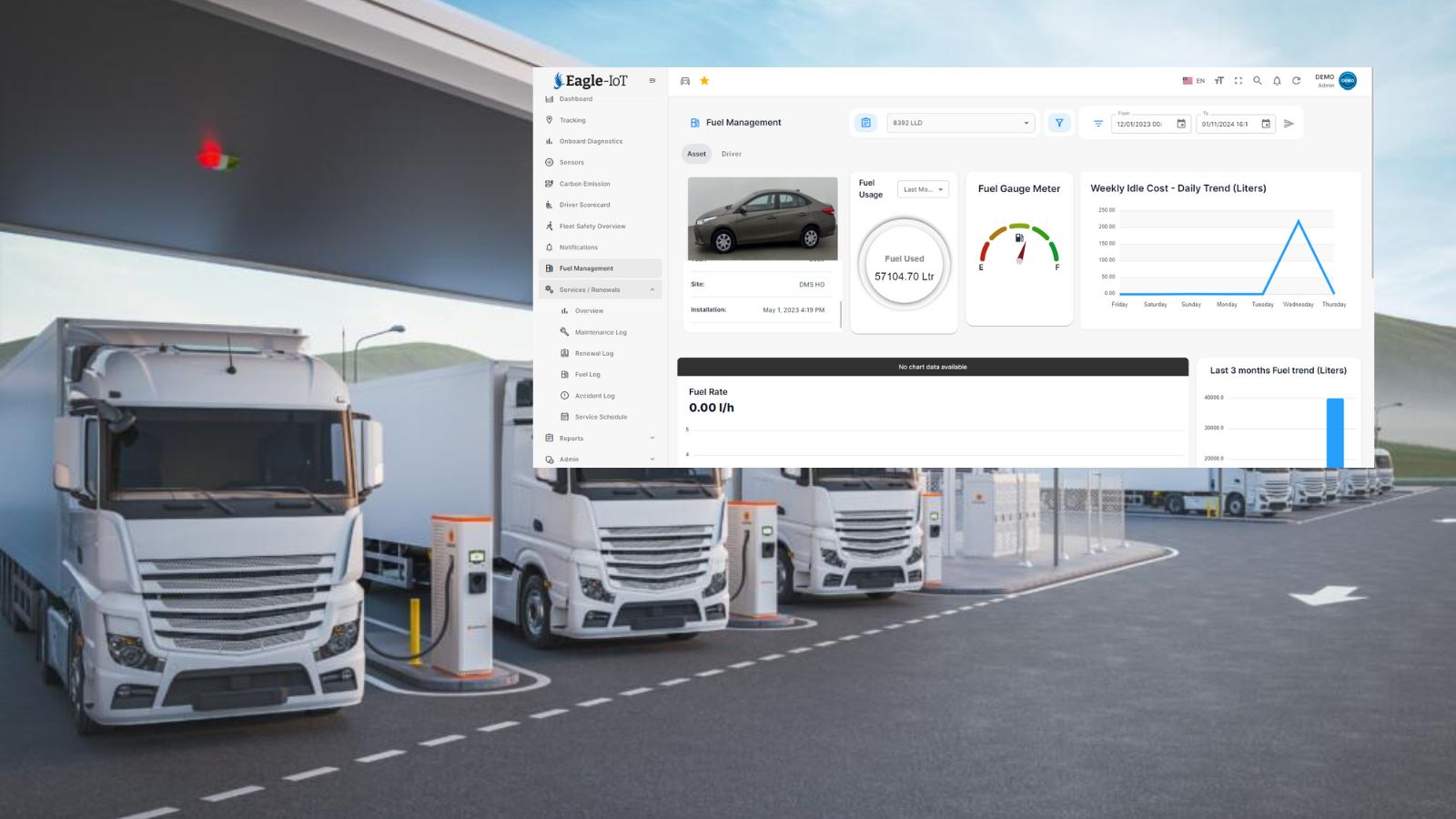
Location Search and Dispatch
In large construction projects, time is money. The ability to quickly locate and dispatch the nearest vehicle to a job site can significantly reduce delays and improve operational efficiency. The location search feature allows users to input coordinates or search by location name to identify specific areas on the map. Once a location is identified, Eagle-IoT premium users can take advantage of the
“dispatch nearest vehicle” feature.
This advanced functionality leverages real-time data to calculate the closest available vehicle, considering factors like route distance and estimated arrival time. For example, if a vehicle needs to transport materials from a warehouse to a job site, the system will automatically identify the best-suited vehicle based on proximity and traffic conditions. This feature eliminates manual guesswork, ensuring that vehicles are utilized efficiently and downtime is minimized.
Multiple Geofence Creation and Management: Tailoring Geofences for Specific Needs
One of the key advantages of a modern fleet management platform is the ability to create and manage multiple geofences simultaneously. Construction companies often manage multiple sites, each with its own operational needs. For instance, a fleet manager might create a geofence around a high-traffic construction zone to monitor vehicle movement and enforce speed limits, while another geofence around a storage yard might focus on tracking equipment arrival and departure times.

Each geofence can have unique settings, such as restricted zones, where unauthorized vehicle entry triggers an alert, or speed zones that limit vehicle speed within certain boundaries. These customizations enhance security, enforce compliance with site-specific safety regulations, and optimize the flow of vehicles and equipment across various locations.
By leveraging multiple geofences, construction companies can significantly reduce the risk of accidents, theft, and unauthorized use of vehicles or equipment.

Route Planning and Sharing: Navigating Efficiently to Save Time and Fuel
Efficient route planning is crucial for minimizing travel time, fuel consumption, and ensuring timely deliveries of materials to job sites. After a vehicle is dispatched, the fleet management system generates optimized directions and a map link, which can be shared with the driver for seamless navigation. This feature simplifies communication and reduces the risk of drivers getting lost or taking inefficient routes. In addition to route planning, the system offers real-time updates, enabling fleet managers to adjust routes dynamically based on traffic conditions, road closures, or project requirements. By optimizing routes, construction companies can save on fuel costs, reduce vehicle wear and tear, and ensure that materials and personnel arrive on time, enhancing overall productivity.
History Playback and Trip Analysis: Gaining Insights from Past Journeys
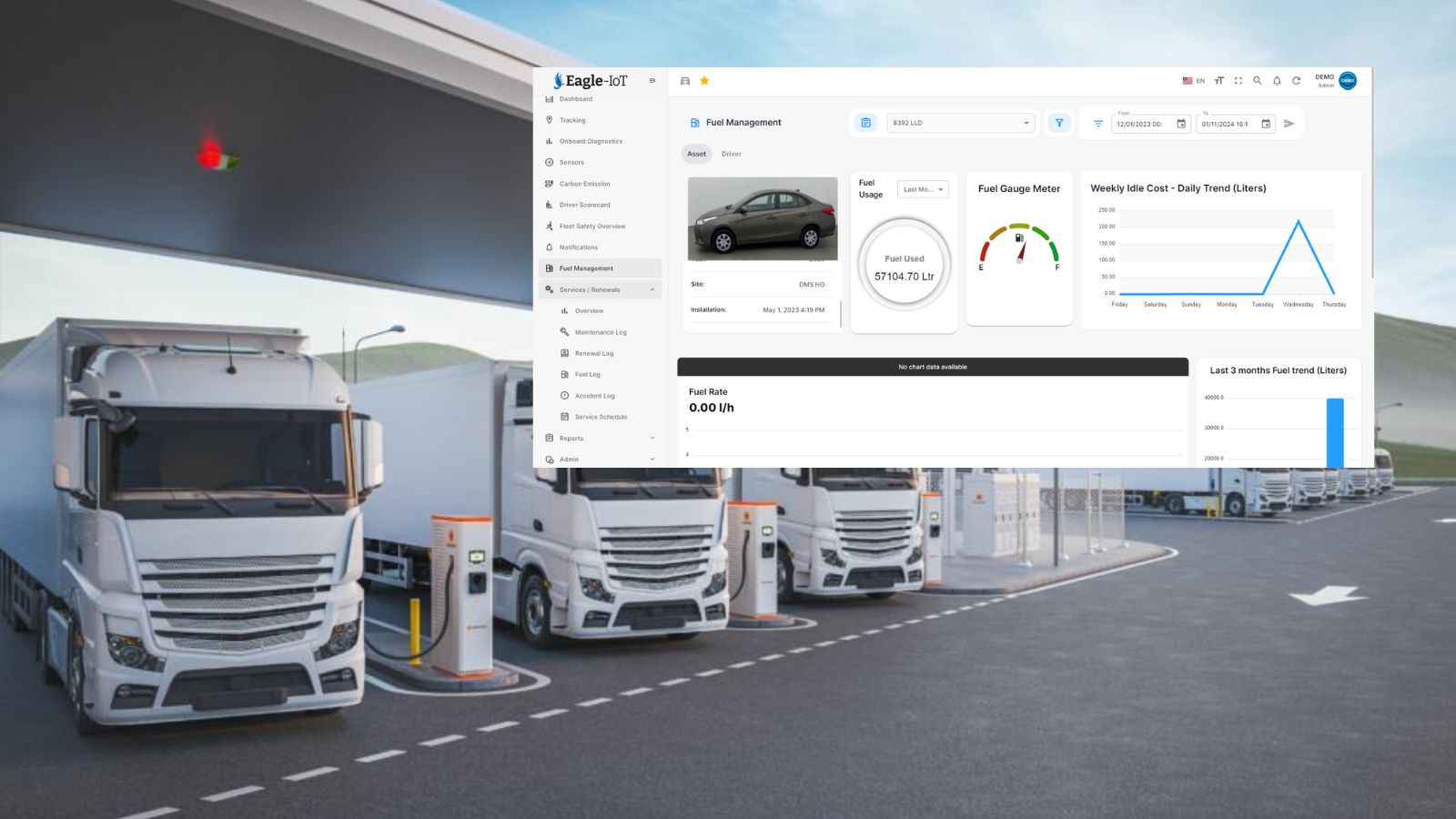
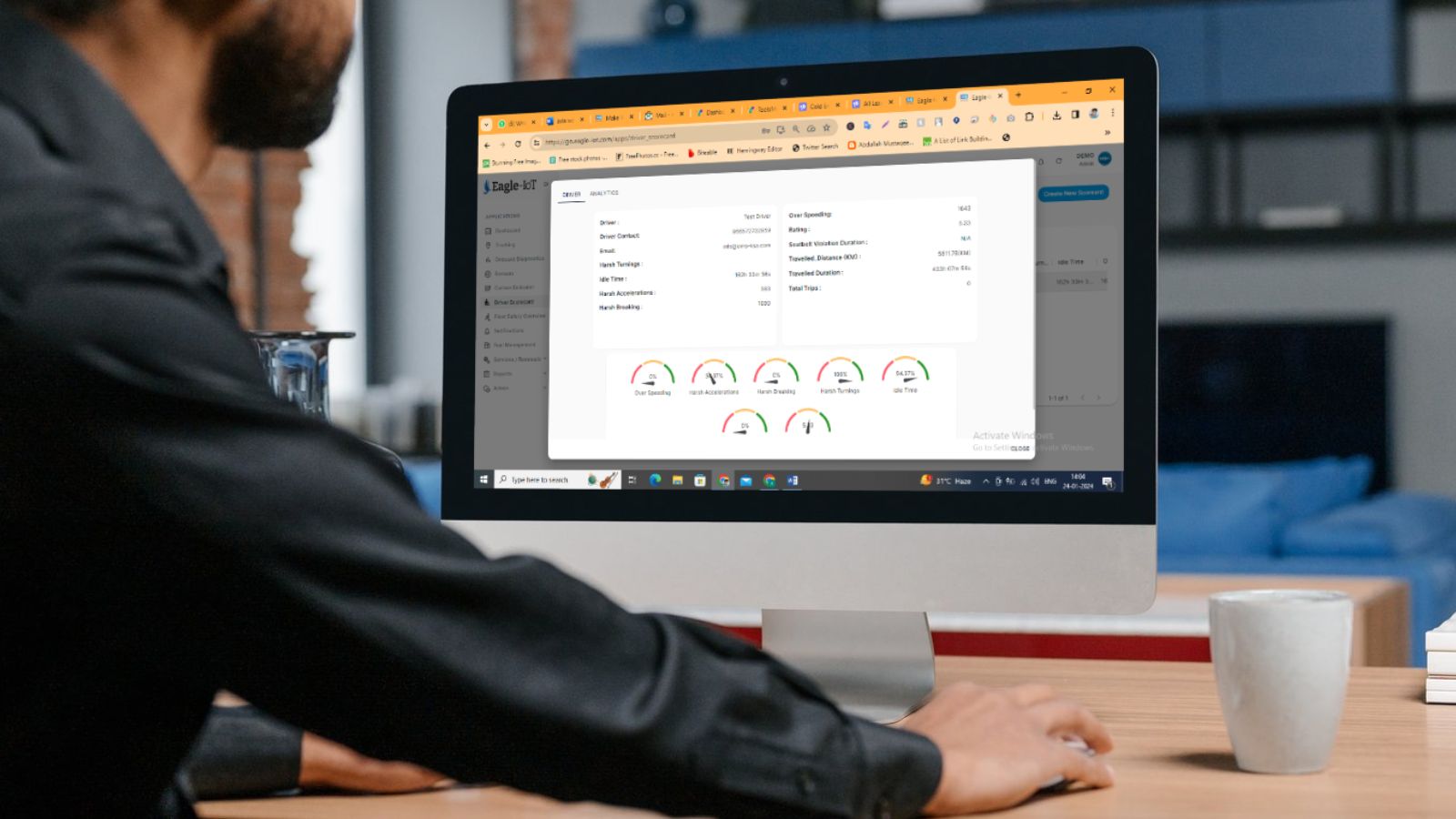
Understanding how your fleet is being utilized is essential for improving efficiency and reducing costs. The history playback feature allows fleet managers to visualize and analyze past vehicle trips. Whether you want to review the performance of a vehicle during a particular project or evaluate how efficiently vehicles are being used, this feature provides a wealth of data for informed decision-making.
Users can generate trip histories for specific date ranges or use predefined filters like “today” or “yesterday” to quickly access relevant data. The system plots each trip on the map, allowing users to see the routes taken, vehicle speed, idling time, and other critical metrics.
Trip Plotting and Data Analysis
Trip plotting offers a detailed visualization of a vehicle’s journey, with each trip represented by a unique color for easy identification. Along the route, information balloons provide additional insights, such as:
Green Balloons: Indicate vehicle movement, showing where and when the vehicle was in motion.
Blue Balloons: Signify idling periods, allowing fleet managers to analyze idle time and fuel wastage.
Red Balloons: Represent ignition off, marking the end of a trip or long stops.

This granular data helps fleet managers pinpoint inefficiencies, optimize routes, and identify areas for improvement, such as reducing idle time or ensuring vehicles follow the most efficient routes.
Incomplete Trip Analysis and Reanimation
For vehicles currently in motion, users can utilize the “plot all” function to visualize the entire recorded history of the trip. This ensures that even incomplete trips are captured and analyzed, providing a continuous flow of data for fleet management.
If needed, users can “reanimate” the trip to simulate vehicle movement along the recorded route. This feature is particularly useful for investigating incidents or analyzing driver behavior over time.
Multi-Vehicle Tracking and Picture-in-Picture: Monitoring Multiple Projects Simultaneously
Construction projects often require managing several vehicles across multiple locations, which can be challenging without the right tools. The platform’s multi-vehicle tracking and picture-in-picture functionality allow fleet managers to monitor up to four vehicles simultaneously.
For example, if a fleet manager is overseeing multiple construction sites, they can open each vehicle’s tracking information in separate windows. This feature provides a consolidated view of vehicles at different locations, ensuring that fleet managers can effectively monitor and manage all assets in real-time.


Conclusion: Optimizing Fleet Management for Construction Success
In the construction industry, time, resources, and efficiency are critical to success. By leveraging advanced features like geofencing, location search, route planning, trip analysis, and multi-vehicle tracking, construction companies can gain greater control over their assets, improve operational efficiency, and reduce costs.
Geofencing ensures vehicles and equipment stay within designated areas, while location search and dispatch features save valuable time in getting the right vehicle to the right place. Route planning optimizes navigation, and trip analysis provides actionable insights to improve fleet performance. With multi-vehicle tracking, fleet managers can oversee complex projects spread across multiple sites, ensuring that all assets are operating at their peak potential. Platforms like Eagle-IoT offer construction companies the tools they need to not only manage but optimize their fleets, empowering them to make data-driven decisions that enhance productivity and profitability. By implementing these solutions, construction companies can stay ahead of the competition and ensure the success of their projects.